Red Team Cyber Security Definition

Cyber exercise adapted from.
Red team cyber security definition. They are also responsible for recording scores for the blue teams given by the green team and red team on usability and security respectively. You ve invested in your cyber security program but do you know how well it performs under pressure. A red team is a group that helps organizations to improve themselves by providing opposition to the point of view of the organization that they are helping. It s vital for the red and blue teams to work together against cyber criminals so cyber security can be improved.
Nist sp 800 53 rev 4. This means comprehensive testing of your business s technical landscape as well as fully testing your people and physical security controls. Red team exercise definition. They are often effective in helping organizations overcome cultural bias and broaden their problem solving capabilities.
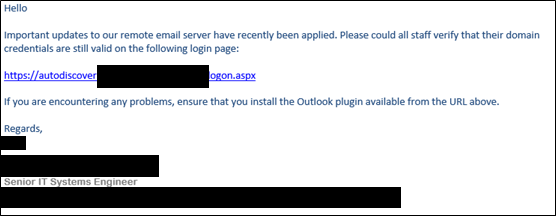
Sometimes the red team may find holes that the blue team has completely overlooked and it s the responsibility of the red team to show how those things can be improved. Red team assessment test your security against real world attacks without the risks of negative headlines. The white team also reads the security reports and scores them for accuracy and countermeasures. If a security team uses standard pentesting tools runs their testing for only one to two weeks and is trying to accomplish a standard set of goals such as pivoting to the internal network or stealing data or getting domain admin then that s a penetration test and not a red team engagement.
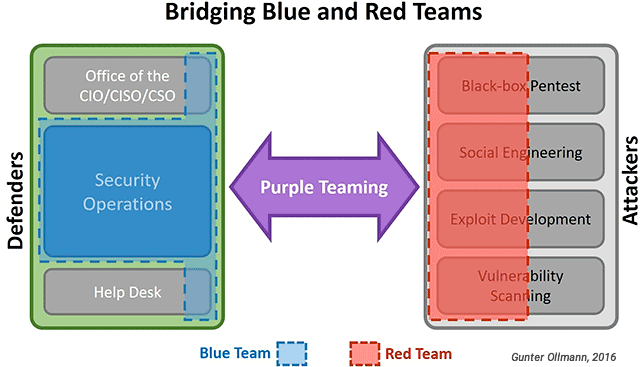
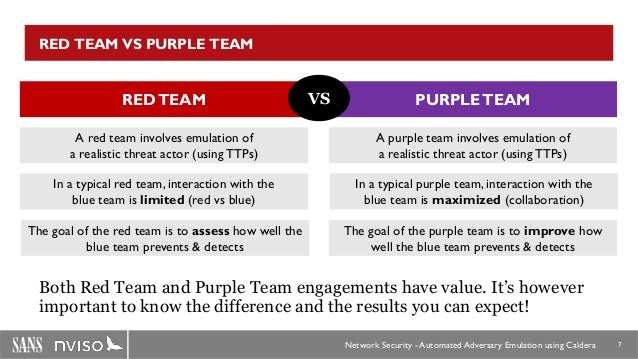
Red team security offers full force red teaming addressing cyber attacks social engineering and physical security in testing threat profiles. Blue team members are by definition the internal cybersecurity staff whereas the red team is the external entity with the intent to break into the system the red team is hired to test the effectiveness of blue team by emulating the behaviors of a real black hat hack group to make the attack as realistic as chaotic as possible to challenge. The team who oversees the cyber defense competition and adjudicates the event. Red team blue team and purple team july 23 2016 by pierluigi paganini in military jargon the term red team is traditionally used to identify highly skilled and organized groups acting as fictitious rivals and or enemies to the regular forces the blue team.
Teaming is a cybersecurity exercise that fully simulates a real life attack to help measure how well an organization can withstand the cyber threats and malicious actors of today. A red team serves as the attacker in this simulation using the same techniques and tools of hackers to evade detection and test the defense readiness of the internal. Definition of white team.